Autel Robotics Data Security White Paper — European Union
Updated: September 2025
Autel Robotics complies with the European Union Data Act, the General Data Protection Regulation (GDPR) and other relevant regulations to help ensure the security, accessibility, and portability of user data throughout its entire lifecycle, including generation, storage, transmission, transfer, and deletion. Users remain in control of their data. Any data access, export, or sharing requires explicit user consent. Upon request, data can be obtained and exported in a structured, commonly used, and machine-readable format. User data generated in the European Union/European Economic Area (EU/EEA) is stored in cloud facilities located within the European Union. Data is encrypted at rest with AES-256 and in transit with TLS 1.2 or above. Furthermore, organisational and technical measures, including least privilege access control and tenant isolation, are implemented.
This White Paper and associated policies (e.g., the Privacy Policy) may be updated from time to time to reflect changes in Autel Robotics' services, personal data processing practices, or applicable laws. We recommend that you review the latest version regularly. Prior to using our services, please read this white paper and the relevant policies carefully and make sure you fully understand them. If you do not agree to any of the contents, you must discontinue use of the relevant services.
1. Key Security Features
1.1 Device Security
1.1.1 Chip and Hardware Security
Chip and hardware security form the primary defense for unmanned aerial vehicle (UAV) security.
Autel Robotics UAVs utilise Arm®-based processors. Within these chips, physical isolation is implemented through hardware-enforced separation and partitioning into security domains.
- TrustZone Technology: This technology employs hardware-based static isolation to partition the system into the secure world and the non-secure world, thereby isolating hardware resources across security domains.
- A security domain can independently handle sensitive data operations (e.g., key management, encryption/decryption of the UAV's album), without application layer involvement. This reduces performance overhead and enhances security and stability.
1.1.2 Firmware Security
Autel Robotics UAVs support over-the-air (OTA) updates for deploying new features, security patches, and bug fixes. Update packages are cryptographically signed and encrypted by Autel Robotics prior to release. The UAV decrypts and verifies the cryptographic signature of update packages. The update process commences only after successful verification. The update system incorporates a hardware-based anti-rollback mechanism to help prevent reversion to vulnerable firmware versions.
This secure update process helps prevent the installation and execution of unauthorised or malicious code on Autel Robotics UAVs, ensuring the reliability of UAV software.
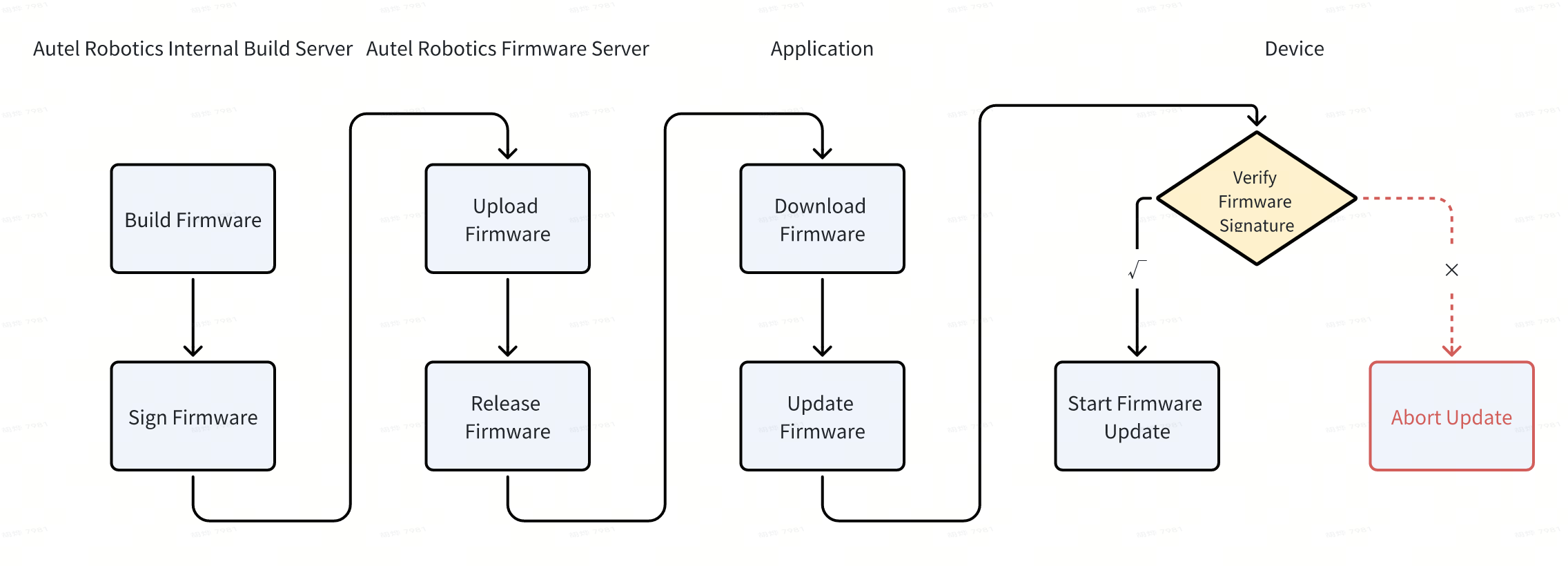
1.1.3 Device Data Security
The UAV system generates, processes, and stores data during operation. The specific data types and their detailed descriptions are as follows:
| Data Type | Description | Format | Storage Location | Usage |
|---|---|---|---|---|
| Flight records | The environmental and real-time information of the UAV collected during flight, e.g., current altitude, latitude and longitude, power voltage. This data contains no personal data. | CSV/JSON | Remote controller or Autel AthenaOS cloud server |
Remote Controller + UAV Scenario: - Data can be uploaded to the Autel Robotics cloud server via the application only after the user logs in to their Autel account and grants authorisation. Users may also independently upload data to designated third-party platforms. - If authorisation is not granted, the relevant data remains stored locally on the remote controller, and Autel Robotics does not proactively access users' flight records. Nest + UAV Scenario: - Data is automatically uploaded to the Autel AthenaOS cloud server and stored in the dedicated cloud storage space of the associated organisation, protected with private read-write access controls. - Autel Robotics does not access user flight records. |
| Flight logs | The UAV system generates log files during operation for identifying and resolving system errors. | TXT/LOG | Device side | Remote Controller + UAV Scenario: - Data can be uploaded to the Autel Robotics cloud server via the application, generating a unique link (QR code), only after the user logs in to their Autel Robotics account and grants authorisation. - If authorisation is not granted, the data remains stored locally on the device, and Autel Robotics does not proactively retrieve user flight logs. Nest + UAV Scenario: - Data is stored locally on the device and can be downloaded from the device to local storage via Autel AthenaOS only after the user logs in to their associated organisation's Autel AthenaOS account. - Autel Robotics does not access device logs. |
| Media data | Photos or videos captured by the user | JPG/MP4 (may also include formats such as PNG, MOV) | UAV or Autel AthenaOS cloud server |
Remote Controller + UAV Scenario: - Users can preview or manually download media data through the application, or access media data on the microSD card using a card reader. If the security encryption feature is enabled, users must enter the password to access the media data. Nest + UAV Scenario: - Upon mission completion, data is automatically uploaded to the Autel AthenaOS cloud server and stored in the dedicated cloud storage space of the associated organisation, protected with private read-write access control mechanisms. - Data can be previewed or downloaded to local storage via Autel AthenaOS only after the user logs in to their associated organisation's Autel AthenaOS account. Autel Robotics does not access users' media data. |
| Update package | UAV system firmware | ZIP/BIN | Device side | The firmware is cryptographically signed and encrypted by Autel Robotics, and transmitted to the device via the application or Autel AthenaOS. |
- Log Deletion
Flight logs are generated by the UAV during operation, recording the status information of various modules. Autel Robotics provides the user with a manual deletion feature to help ensure compliance with data confidentiality requirements.
- Security Password
The user can set a security password to protect the UAV’s media data and assets. When security password protection is enabled, the user must enter the password to decrypt UAV media data when accessing it via the remote controller.
The security password protection feature helps prevent unauthorised access to media data stored on the UAV. For instance, this helps protect the user's media data if the UAV is transferred to a third party or is lost.
The security password is neither stored within the application nor uploaded to the Autel Robotics cloud server. Decryption can be performed only after the UAV has landed.
1.1.4 User Data Access and Deletion
Autel Robotics states that users remain in control of their data. No user data is accessed or used by Autel Robotics without the users' explicit consent. The following section details the specific methods for data access, download, and deletion, along with any associated limitations.
- Data Access Methods
Users may access their personal data through the following channels. All access requires the user's explicit authorisation:
- Mobile Application (APP): When controlling the UAV via official applications such as Autel Enterprise, Autel Sky or Autel Voyager, users can view device status, flight logs, and media files within the APP. Sensitive data, such as flight logs, is accessible only within a user-selected date range and after the user manually enables authorisation in the APP.
- Web Platform: When utilising the Autel AthenaOS for centralised control and management, users can access fleet flight data, mission records, and device management information via the web interface, facilitating remote data retrieval and scheduling. Such centrally managed data is unavailable to users who do not use Autel AthenaOS.
- Developer API: In scenarios with the Mobile SDK enabled, developers can access real-time video streams, sensor data (e.g., battery level, GPS coordinates, flight speed), and stored media files through API operations. This supports automated data acquisition, third-party application development, and system integration.
- Data Download Methods
Users can export or download their personal data using the following methods:
- Flight Record Export: Within the APP, navigate to "More > Logs", select the "Aircraft/Remote Controller/APP" module to generate a download QR code, or perform physical extraction via an SD card (requires formatting the SD card and creating a log trigger file according to the specified steps). Flight records can be exported in CSV format, facilitating data analysis and archiving.
- Media File Download: By default, photos, videos, and other media files are stored in the UAV's internal storage or on an SD card. Users can download them directly to a mobile device via the APP, or copy the files to a computer using a card reader. Developers can invoke preview or complete download functions for media data using the SDK.
- Sensor and Device Data: Using the Mobile SDK, developers can retrieve real-time sensor data (e.g., voltage, signal strength, altitude) and export it for device status analysis and debugging.
- Data Deletion Mechanism
Data can be deleted using the following methods, in accordance with the principle of "immediate local deletion and time-bound cloud processing":
- Local Data Deletion: Media files and cached data stored on the UAV's internal drive or the remote controller can be manually deleted via the APP or by restoring the device to factory settings. These operations take effect immediately.
- Cloud Data Deletion: All cloud logs and backup data associated with a user's account are automatically deleted when the user deletes their account via the APP. When flight logs are deleted individually from the Cloud, the server will complete processing within 24 hours. Deleted data is removed from the active system but may be temporarily retained in the backup system until the next backup cycle (no longer than 30 days). During this period, the data remains strictly isolated.
- One-Touch Log Deletion: Selecting "Clear All Device Data" in the "Settings > Privacy" section of the APP will immediately delete locally stored UAV logs, remote controller logs, and cached APP data.
- Technical and Service Quality Limitations
Certain data may be temporarily retained due to technical necessities or service requirements, as detailed below:
- After-Sales Service Data: When a UAV is sent for repair, diagnostic logs stored in its internal memory (e.g., sensor data, fault records) will be retained for the duration of the warranty period for troubleshooting purposes. Upon completion of repairs, non-essential data will be purged automatically. If no repair is conducted, such data is not retained. Users must not delete or modify internally stored data without prior authorization, as this may affect the warranty coverage.
- Legal Compliance Retention: Autel Robotics may retain relevant data as required by laws and regulations. In such cases, data access is strictly restricted, and the retention period does not exceed the legally mandated timeframe.
- Backup System Isolation: Following cloud data deletion, and due to backup technology constraints, data may be stored in isolation within the backup system until the next cleanup cycle. During this time, the data is inaccessible to any system function.
1.2 Communication Security
Autel Robotics places a high priority on the security of its UAV communication systems. The primary communication transmission solution employed by Autel Robotics is SkyLink. Select models within the EVO Max series currently support 4G communication. This section elaborates on the security features of both solutions.
1.2.1 SkyLink Communication Security
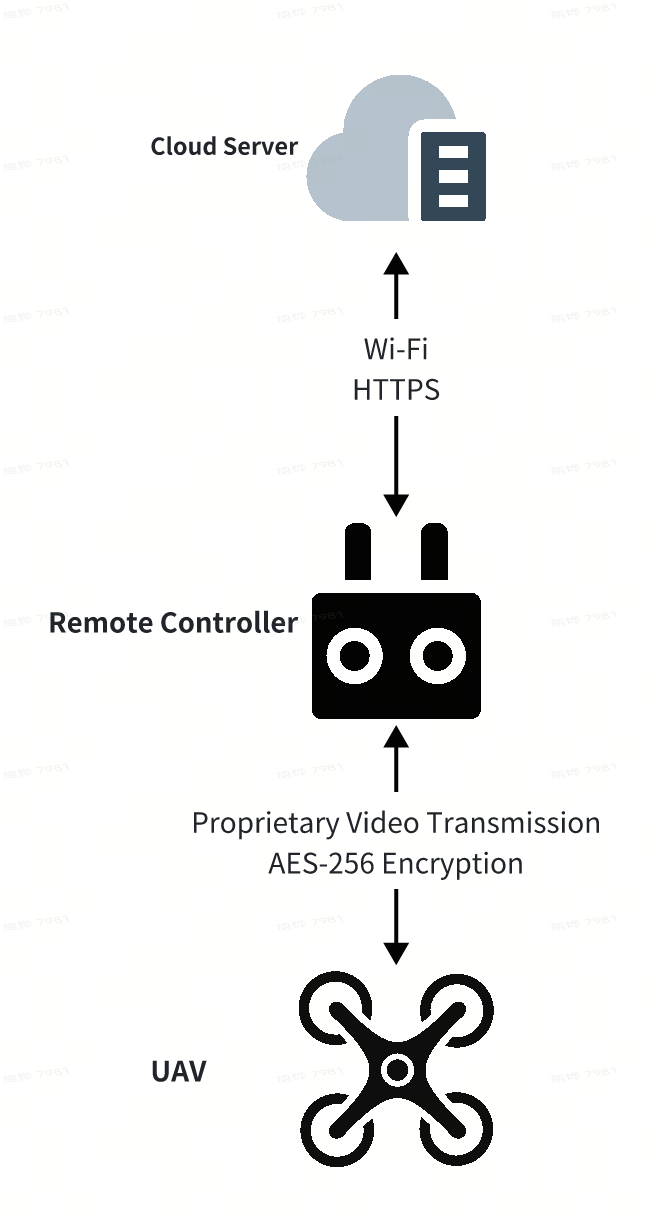
SkyLink is a proprietary protocol developed by Autel Robotics, featuring built-in security mechanisms. This communication solution is implemented across all UAVs manufactured by Autel Robotics. Its control link is encrypted using the AES-256 algorithm. The session key used for encryption is generated by a random number generator upon each UAV startup, ensuring that a unique key is used each time. Furthermore, the UAV's video transmission is also encrypted using the AES-256 algorithm.
SkyLink's communication mechanism, leveraging techniques such as secure key agreement and communication encryption, effectively mitigates threats including communication hijacking, man-in-the-middle (MITM) attacks, replay attacks, and eavesdropping.
1.2.2 4G LTE Communication Security
Currently, Autel Robotics' 4G LTE communication is implemented primarily in select models of the EVO Max series. The UAV and the remote controller communicate via a relay server. Prior to establishing a relayed 4G connection, a SkyLink connection is first established between the UAV and the remote controller. Once the SkyLink connection is established, information is exchanged between the UAV and the remote controller over the secure SkyLink channel. After this exchange, the relayed 4G connection is established. When establishing the 4G communication link, the UAV and remote controller will authenticate each other using the information exchanged earlier to help prevent unauthorised access or erroneous connections. The 4G communication link is encrypted using the mobile operator's security protocols, effectively safeguarding users against both near-field and remote communication hijacking, MITM attacks, replay attacks, and eavesdropping.
1.3 Application Security
Autel Robotics' industry-grade applications, such as Autel Enterprise and Autel Voyager, are developed on the Android platform. As core components of the UAV system, these applications handle tasks including interacting with the UAV, displaying imagery captured by the UAV, controlling the UAV, image editing, providing user registration and login functions, and interfacing with cloud services. To ensure application security and prevent sensitive information leakage and malicious attacks, Autel Robotics has implemented multi-layer security hardening measures within these applications.
In addition to applications, Autel Robotics provides various software development kits (SDKs). Users can customise applications based on their specific requirements. These SDKs can be used either individually or in combination to fulfill diverse needs.
The following sections detail the security settings, privacy protection strategies of the applications, and the relevant security configurations for the SDKs.
1.3.1 Application Hardening
- Decompilation Protection
To prevent attackers from acquiring business logic (e.g., communication, encryption, and UAV control logic) through code decompilation, Autel Robotics has implemented the following protection measures in its applications:
- Code obfuscation and packing are applied to increase the difficulty of reverse engineering, thereby preventing attackers from easily comprehending the core logic.
- For code handling sensitive user information, advanced virtual machine (VM) protection technology is utilised. This technology converts the original executable code into customised bytecode, which is then executed on a VM, thereby providing an additional layer of security.
- Dynamic Library Encryption Protection
As critical components of the application, dynamic libraries' security directly impacts the overall system stability. Autel Robotics has implemented the following protective measures for dynamic libraries:
- Assembly code within dynamic libraries is compressed and encrypted to thwart direct reverse engineering analysis.
- The Executable and Linkable Format (ELF) information of dynamic libraries is protected against tampering and extraction.
- Dynamic libraries are decrypted upon loading, and the code is purged from memory immediately after use to minimise exposure risk.
- Dynamic Runtime Protection
Autel Robotics incorporates a dynamic defense mechanism based on anti-debugging techniques to provide comprehensive protection for the application during runtime:
- Active detection and monitoring mechanisms safeguard critical system processes, preventing attackers from debugging the application.
- Key functions are periodically polled to detect any hooking attempts and prevent unauthorised operations.
- Common debugging tools and injection methods are monitored to defend against dynamic debugging and code injection attacks.
- Logical functions within key modules are replaced and hidden to prevent hooking or tampering.
- Local Resource Protection
To ensure the security of local data, Autel Robotics has implemented a comprehensive data encryption mechanism at the Android file system level:
- All file operations (e.g., flight logs, SharedPreferences, databases, application logs) are encrypted to prevent data leakage.
- Binary files are packaged with integrated anti-debugging features and cryptographically signed to prevent the distribution of tampered applications by third parties.
- Keys and passwords used for UAV interaction are obfuscated and further secured using VM protection technology to prevent the leakage of sensitive information.
- Integrity Protection
All contents of the Autel Robotics application package are cross-checked to ensure the integrity and authenticity of the application:
- Both the application package contents and its checksum are encrypted, enabling the timely identification of unofficial or tampered applications.
- If an unofficial or tampered application is detected, the system prompts the user to exit and blocks potential threats, such as malicious advertisements and trojans.
- Front-end Code and Critical Data Protection
- Front-end code is obfuscated and encrypted to prevent source code leakage and exploitation.
- Key credential parameters are encrypted. Sensitive key data is dynamically fetched from the server side to the client, rather than being stored locally on the frontend. This approach reduces the risk of key capture and misuse, ensuring security during transmission and storage.
- The use of WSS and HTTPS is enforced for all communication between the client and server to prevent MITM attacks and network sniffing.
1.3.2 Application Data Security
This section details the data security strategies for Autel Robotics' industry-grade applications across multiple dimensions, including communication, local data storage, data synchronisation, and privacy settings.
Autel Enterprise enables direct interaction with industry-grade multi-rotor UAVs, whereas Autel Voyager is designed for direct interaction with vertical take-off and landing (VTOL) fixed-wing UAVs. Both applications support UAV system communication, interaction control, real-time image transmission and display, user information management, and intelligent mission execution. They provide features that meet industry-grade security requirements.
| Device Information | Content and Usage | Collection Time (with user consent) |
|---|---|---|
| UAV location | This information is used for the flight control system to refresh and verify no-fly zone data. | At power-on |
| Device information | This includes the product serial numbers of your Autel Robotics devices paired with the application, including those of the UAV, gimbal, remote controller, and battery. It is used for device activation and device-related requests, such as the "Fly Freely" service. | A one-time device activation is required before first use, binding the device to your corresponding Autel Robotics user account. Additionally, a one-time network request is generated when you actively use functions like the "Fly Freely" insurance inquiry. |
| Device positioning | This is the location information of the Autel Robotics device
paired with the application. This information is provided to third-party map frameworks to display your device's real-time location on the map. The map interface is presented within the "Find UAV" feature and the map function on the flight interface. |
When using map services. |
| Experience data | Non-personally identifiable behavioural data, including: - Stack trace information from application crashes. |
Collected during use of the relevant features. |
| Flight records | Detailed flight data generated in real time by the application
and flight control system, including: - Flight path and UAV attitude data - Camera and gimbal status - Battery status - Remote controller and video transmission status - Visual and sensor system status This data enables users to synchronise historical flight data across different devices. |
When users actively synchronise flight records to the Cloud. |
| Flight logs | Log files generated during UAV system operation, used for
post-sales product issue analysis. By default, log files are stored locally on the device; users can initiate an upload to the Cloud. |
/ |
| Videos/Photos | Captured photos and videos are stored in the UAV's internal
storage. Users can enable security password protection for these files. Preview is available via the paired application (when password protection is disabled); files are downloaded to the remote controller only after manual selection. |
/ |
| Dynamic flight data reported to the Civil UAS Operation
Management System (UOM) Applicable only in Chinese Mainland |
Mandated by the "Announcement on Issuing the Requirements for Reporting Flight Dynamic Data of Civil Unmanned Aerial Vehicles," published November 15, 2024. | Upon power-on. |
1.3.3 Autel Robotics SDK Security
Autel Robotics provides various SDKs, such as the Mobile SDK and Payload SDK, enabling users to customise their applications based on specific requirements. These SDKs can be utilised either individually or in combination to address diverse development needs. The security and privacy configurations for the SDKs include:
- Privacy and Security Settings: Ensure the SDK's handling of user data complies with privacy terms to prevent leakage of sensitive information.
- Open-Source Status: Clarifies the SDK's open-source status and relevant licensing agreements, aiding developers in understanding usage constraints.
- Data Encryption: Employs encryption for all internal data transmission and storage within the SDK to safeguard data.
For SDK development documentation, please refer to: https://developer.autelrobotics.com/
1.4 Cloud Security
1.4.1 User Account Security
All Autel Robotics applications are deployed with an integrated account system, encompassing the Developer Center, Online Store, and value-added services. Other applications perform account operations through embedded web pages and relevant APIs. Autel Robotics employs the following measures to safeguard user account security:
- Account Center User Management System: This system is capable of detecting malicious activities, including anomalous logins, brute-force attacks, and malicious registrations. For example, an account will be temporarily locked after five consecutive failed verification code attempts.
- IP Restrictions: To mitigate large-scale malicious requests against the services, the User Center implements IP restriction measures and blocks identified malicious IP addresses.
- User Information Encryption: Critical user information in databases is encrypted using techniques such as RSA and salted hashing. Additionally, HTTPS encryption secures network transmission, ensuring the security of account information during both storage and transmission.
1.4.2 Server Security
This section elaborates on Autel Robotics' server security from three perspectives: host security, web application security, and operational security.
- Host Security
Autel Robotics' internet services are primarily cloud-deployed. Consequently, the security of these services is largely dependent on the cloud service providers. Autel Robotics' cloud service providers include Amazon Web Services (AWS) (for regions outside Chinese Mainland) and Huawei Cloud (for Chinese Mainland).
- AWS is renowned for its security credentials and high reliability. AWS has obtained ISO/IEC 27001, ISO/IEC 27017, and ISO/IEC 27018 certifications.
- Huawei Cloud is committed to providing secure and trustworthy cloud services and has attained
various internationally recognized certifications and adopted various compliance standards:
- For security-related certifications, it has earned ISO 27001, ISO 27017, CSA STAR Gold Certification, and Classified Protection of Information Security of China's Ministry of Public Security (Levels 3 and 4).
- For the payment card industry, standards and frameworks such as PCI DSS and the NIST CSF are adopted for cybersecurity.
- For privacy-related certifications, it has earned ISO 27018, ISO 27701, BS 10012, ISO 29151, and ISO 27799 certifications, among others.
Autel Robotics prioritizes host security by conducting regular scans of host configurations using specialised tools. Identified vulnerabilities are promptly remedied to maintain a secure posture.
- Web Application Security
Before reaching backend services, network requests traverse multiple layers of security protection designed by Autel Robotics, which include DDoS mitigation with traffic scrubbing, web application firewalls (WAFs), and runtime application self-protection (RASP).
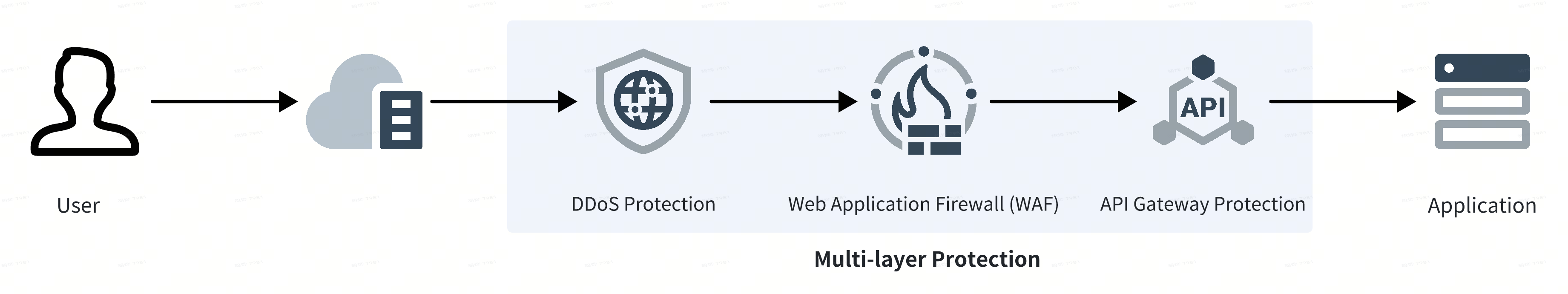
Autel Robotics regularly conducts penetration testing and code analysis on its online applications. Furthermore, the code for UAV-specific applications undergoes rigorous review by security experts to safeguard their security. Should vulnerabilities be identified during these assessments, the development team promptly implements effective remediation measures.
- Operational Security
The operational security of cloud servers is maintained by Autel Robotics' dedicated operations team. This team adheres to Amazon AWS recommended best practices for resource and authorisation management, enforcing the principles of "need-to-know" and least privilege to ensure strict allocation and control of host and system permissions. All server-side operations strictly follow standard operating procedures (SOPs).
Autel Robotics' operations team achieved ISO/IEC 27001 certification in July 2022 and maintains its certification status. The ISO/IEC 27001 certification provides customers with independent verification of their information security management capabilities.
1.4.3 Cloud Services and Data Security
Autel Robotics provides a variety of cloud services for both consumer-grade and enterprise-grade users, storing specific user data solely after obtaining user consent. In compliance with relevant laws and regulations, Autel Robotics has established the Personal Information Protection Specification to govern data storage practices across all applications. Personal information, including but not limited to name, email address, geographic location, and flight records, is encrypted using AES-256 to help protect data.
All data transmissions by Autel Robotics are encrypted to prevent malicious acquisition. Specific measures are as follows: Data communication between web browsers, mobile applications, and servers is secured using TLS v1.2 or above.
2. UAV Security Solutions
2.1 Industry-Grade Security Solutions
Autel Robotics offers a variety of industry-grade UAV platforms, such as the EVO Max and Dragonfish series, alongside industry-grade applications including Autel Enterprise and Autel Voyager, as well as their corresponding cloud services. Autel Robotics' industry-grade security solutions encompass secure communications, encrypted video transmission, device password protection, geofence unlocks for specific devices, and cloud-based services via Autel AthenaOS.
- Multi-rotor UAV + Smart Remote Controller (Autel Enterprise)
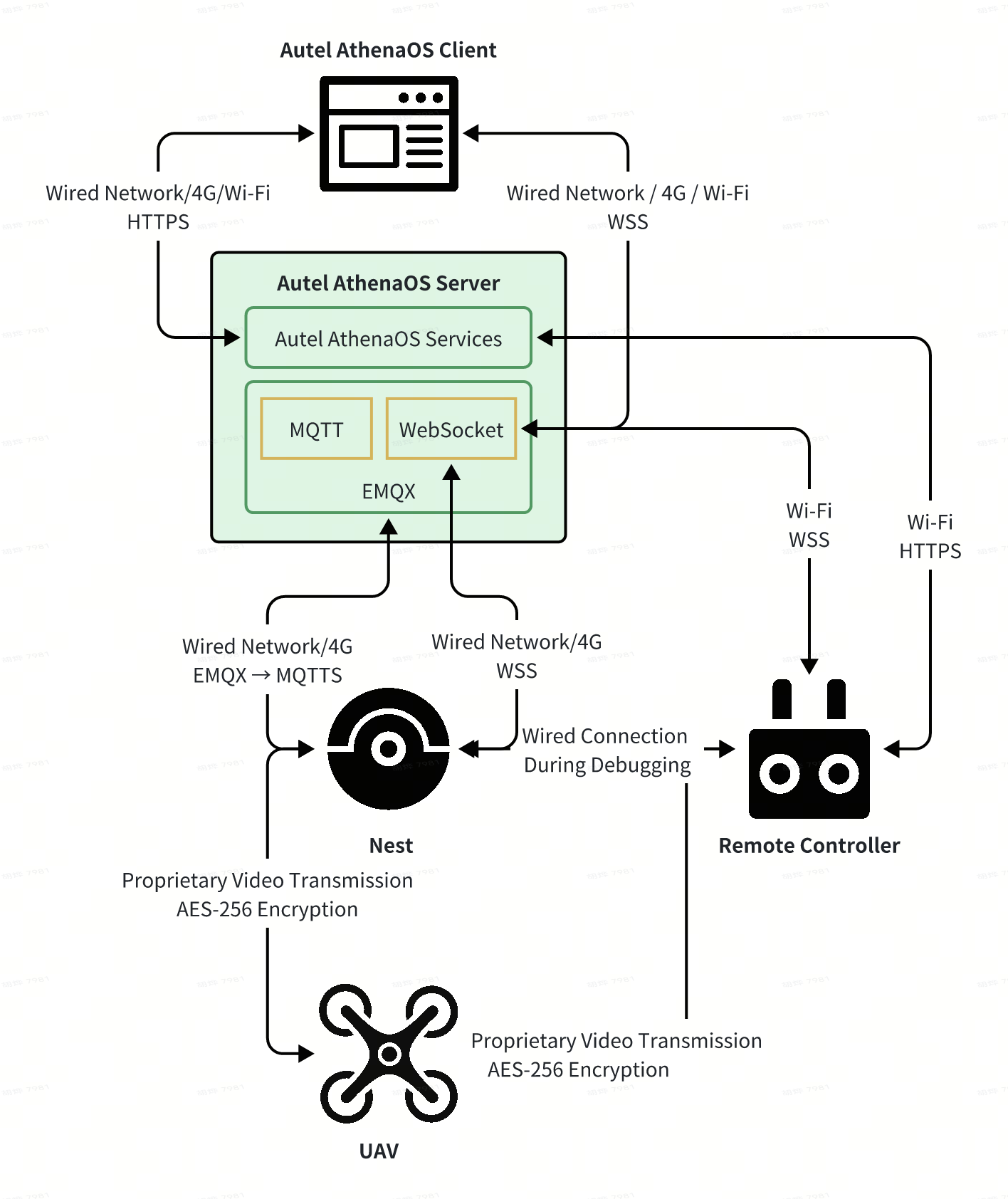
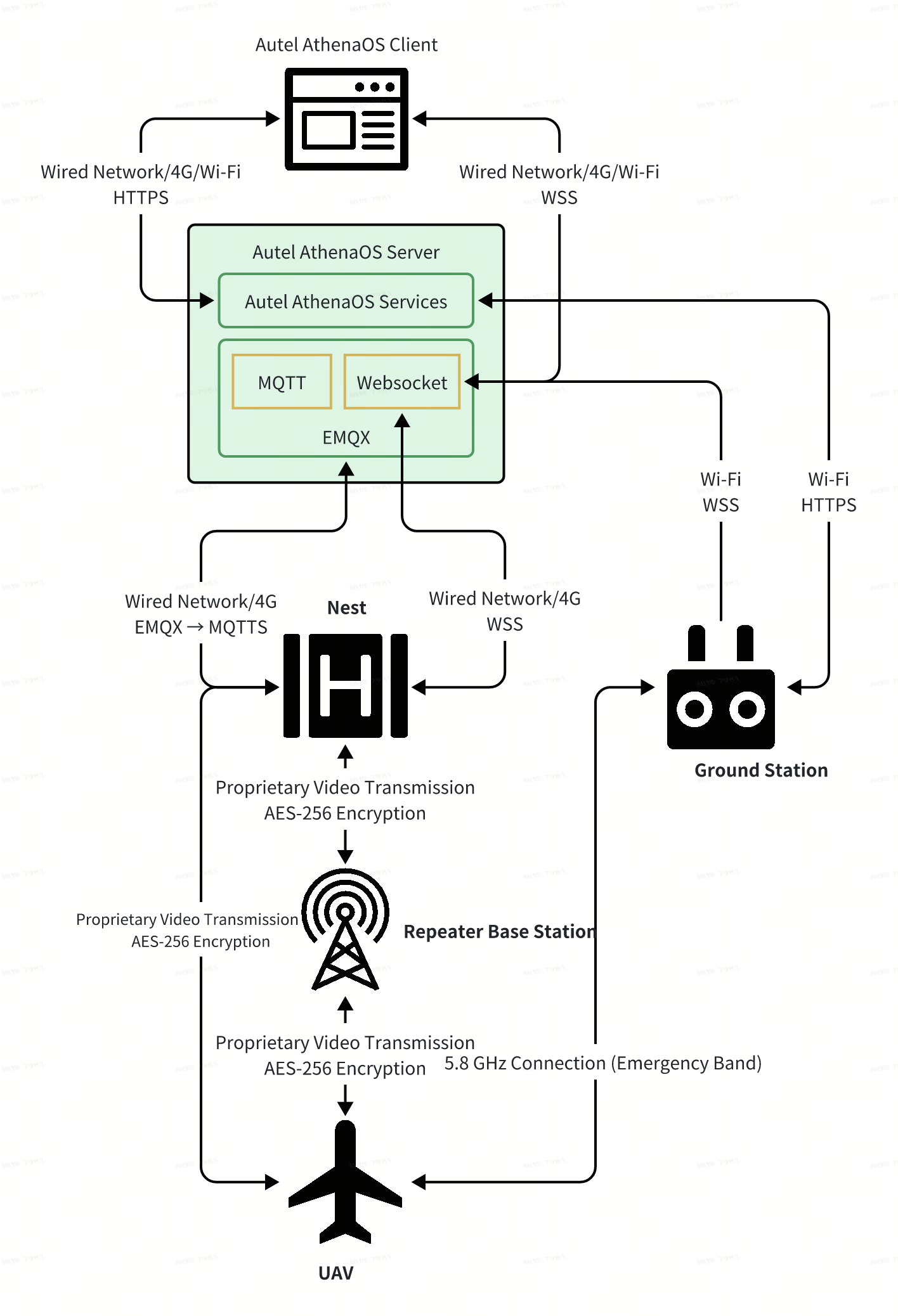
- Multi-rotor UAV + EVO Nest + Autel AthenaOS
- Fixed-Wing UAV + Ground Station (Autel Voyager) + Wi-Fi Base Station/Autel Smart Antenna Transmission (ASAT)
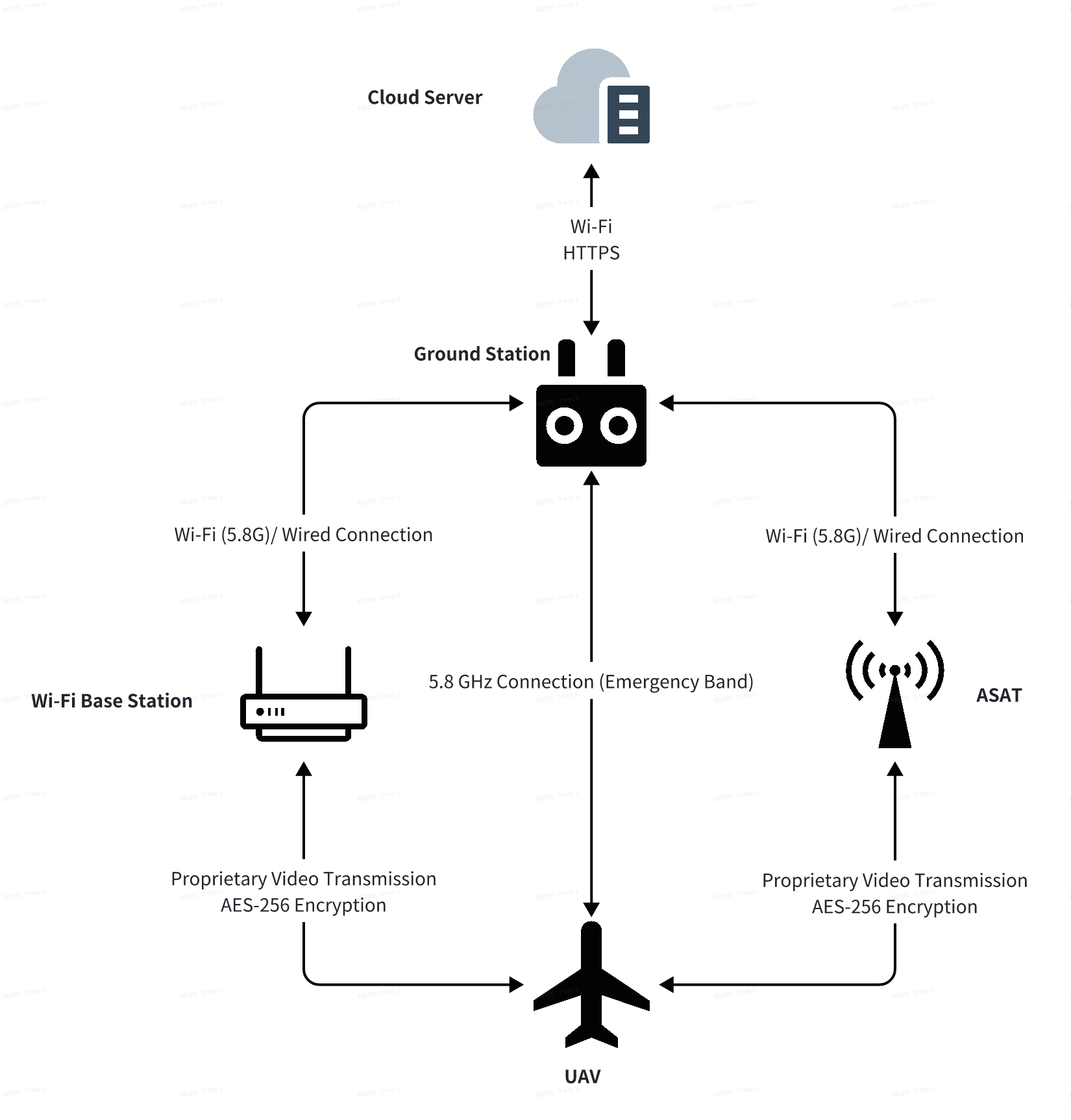
- Fixed-Wing UAV + Repeater Base Station + Fixed-Wing Nest + Autel AthenaOS
Additionally, Autel Robotics also offers private deployment solutions. Under this model, all relevant user data is stored either on user devices or on user-designated servers, catering to specific scenario requirements.
- Generic UAV Application: Compared to the Autel Enterprise or Autel Voyager applications, this version excludes Autel Robotics cloud service features. Data generated during operation is retained solely on the device or on user-designated third-party platforms.
- Autel AthenaOS Private Deployment: When this deployment mode is adopted, Autel Robotics supplies only the necessary offline installation packages and limited technical support. All configuration and daily operational maintenance are managed by the user. Update services are performed solely by manually uploading offline upgrade packages provided by Autel Robotics. All data generated during use is stored exclusively on servers configured by the user.
2.2 Data Storage
Autel Robotics complies with regulations regarding data security isolation in the regions where the data is generated. The following measures are implemented within the user data storage policy to ensure user data hosting complies with applicable regulations:
- Data generated from usage within Chinese Mainland (including activation data, flight records, and Autel AthenaOS service deployment) is stored on cloud servers located within Chinese Mainland, provided by local cloud service providers. Data security is ensured through communication/storage encryption (MQTTS/WSS/HTTPS/AES-256), private read-write access control, and other measures.
- Data generated from usage in the Americas (including activation data, flight records, and Autel AthenaOS service deployment) is stored on AWS cloud servers located in the United States. Data security is ensured through communication/storage encryption (MQTTS/WSS/HTTPS/AES 256), private read-write access control, and other measures.
- Data generated from usage in the EU/EEA (including activation data, flight records, and Autel AthenaOS service deployment) is stored on AWS cloud servers located within Europe. Data security is ensured through communication/storage encryption (MQTTS/WSS/HTTPS/AES-256), private read-write protection, and other measures.
- For other regions, data generated from usage (including activation data, flight records, and Autel AthenaOS service deployment) is currently stored in the same manner as for the Americas.
Autel Robotics ensures isolated storage of user data. Users are authorised to access only the data associated with their account or data permitted within their organisation's scope. User data is not accessed by other users or organisations without unauthorisation.
2.3 Geofencing Security Protocols
Autel Robotics' geofencing system includes both a flight restriction system and an unlock system. The flight restriction system is designed to limit UAV operations within specific zones to ensure flight safety. The unlock system enables partial lifting of flight restrictions after users obtain approval from civil aviation authorities or other airspace regulatory bodies, thereby permitting flight within otherwise restricted areas. Both functionalities are secured by system security mechanisms.
2.3.1 Flight Restriction System Protection
The flight restriction system consists of a geospatial database and flight control functionality. The geospatial database stores geographic coordinate information, such as no-fly zones, warning zones, etc. Static data is embedded within the flight control system, while dynamic data is updated through a designated server. The flight control function, based on the UAV's GNSS information and the geospatial database, determines whether the UAV can enter specific areas and whether any restriction strategies should be applied.
To ensure the reliable operation of the geofencing system, both the geospatial database and the flight control functionality require protection. Autel Robotics implements AES-256 encryption for dynamic data updates to the database during transmission to ensure data integrity.
The flight restriction system processes GNSS information sourced from the UAV's GNSS module and stored in the onboard database. This processing occurs offline without requiring internet connectivity, and user GNSS data is not uploaded. During UAV startup, the geospatial database is refreshed based on the device's GNSS information (only when internet connectivity is available at startup).
2.3.2 Unlock System Protection
When necessary, users can apply to have geographic flight restrictions lifted. Once an unlock application is submitted and approved, the unlock authorisation is securely synchronised to the specific UAV by matching its device serial number. This authorisation is then compared against the UAV's real-time GNSS coordinates to determine if flight restrictions can be lifted. For more information on UAV unlock requests, please visit: www.autelrobotics.com/service/noflight/
3. Privacy Policy
Autel Robotics has established clear terms regarding user data protection and encourages users to read and acknowledge these terms when using Autel Robotics devices, computer software, and cloud services.
For more information about the Privacy Policy, please visit: https://www.autelrobotics.com/privacy/
4. Contact Us
Autel Robotics remains dedicated to the continuous innovation and exploration of UAV functionality and system security, delivering stable, reliable, flexible, and powerful data acquisition and management capabilities to the industry. We recognize that customers choose Autel Robotics not only for our product performance but also for the trust placed in our data security and compliance safeguards.
This White Paper reaffirms our commitment to responsible data stewardship. We are confident that these security standards will not only safeguard customer data but also drive heightened awareness and advancements in data protection across the UAV industry. We will always handle customer data requests with due diligence and respect, while continuously optimising our related mechanisms.
Autel Robotics appreciates your feedback and suggestions to help us further enhance data protection. Should you have any questions, please contact us at support@autelrobotics.com.
Article by Autel Robotics all rights reserved.
